Professional ODM Partner to- Customize
- Design
- Manufacture
Networking products
- Customize
- Design
- Manufacture
Provides OEM / ODM for project based development in quick development time, customized and differentiated HW/SW spec.
More than 230 active SKUs of Ethernet PoE Switches / Unmanaged Switches / Fiber Switches / Industrial PoE Switches / White box switches for our customers to choose from. We offer customization services which consists four categories – Private-label Customization, Advanced Customization, Own Software Customization, and Brand-new Customization. Find more details below.
Advantage and Features
Rubytech ODM Advantage
Low MOQ for selected models, and FREE Software Customization service to make sure the switches work with link partner or IP-relative device. Support easy Customization Platform, so as to implement the Private-Label customization efficiently and economically.
Customization Features
ODM Customization Service for PoE NVR provide ODM flexibility (M-ATX and Mini-ITX), plus scalability (8/16/24-port PoE, 2/3/4/6 HDD tray), instant support (case alarm, PoE auto-reboot mechanism), and easy manageability (CGI / API / SNMP implemented). More than 200 active SKU of Ethernet Switches/NVRs for our ODM customers to choose from.
About ODM SERVICE
ODM Customization
- Experienced HW / SW customization services. More than 200 active SKU of Ethernet Switches/NVRs for our ODM customers to choose from.
- ODM Customization under your brand is no longer a pain point. To offer low threshold, implementing your business become more efficiently and economically.
- Get Golden Sample in one-month, 1st Mass Production in another month and delivery L/T of 4~6 weeks low MoQ for selected 24 models. Create absolutely remarkable standard operation procedure to ODM customer. All products are designed and manufactured in Taiwan.
Risk commitment
- Focuses on ODM / OEM business, and ISO-9001 / ISO-14001/ ISO-27001/ ISO-27034 certified.
- We provide an industrial-grade of product longevity including x86 and switch platform, with PoE/ PoE+/ PoE++(IEEE 802.3af/at/bt) support within compact form factor /dimension of PoE NVRs, so as to provide users with best-fit solutions.
- RubyTech reduces the Tech Support Cost/Time/Effort, moreover, provide differentiation value-adds from All Other Competitors.
- Better Cost/Performance & Customer Satisfaction of PoE NVRs, help to provide more revenue streams from the PoE NVRs.
Why Rubytech?
- Design, Manufacturing, and Service Partner in Taiwan
- More than 40-year experience in the networking industry.
- Experienced HW/SW Customization Services
- ODM Business Focus
- Value-Added Support Platform
- Experienced HW / SW customization services. FREE Tier-2/3 Tech Support for all field problems.
- RubyTech has successful experiences supplying the best cost/performance NVRs to our ODM partners worldwide.
- Being the approved vendor who is now supplying PoE NVRs to Tier-1 and Tier-2 ODM brand customers.
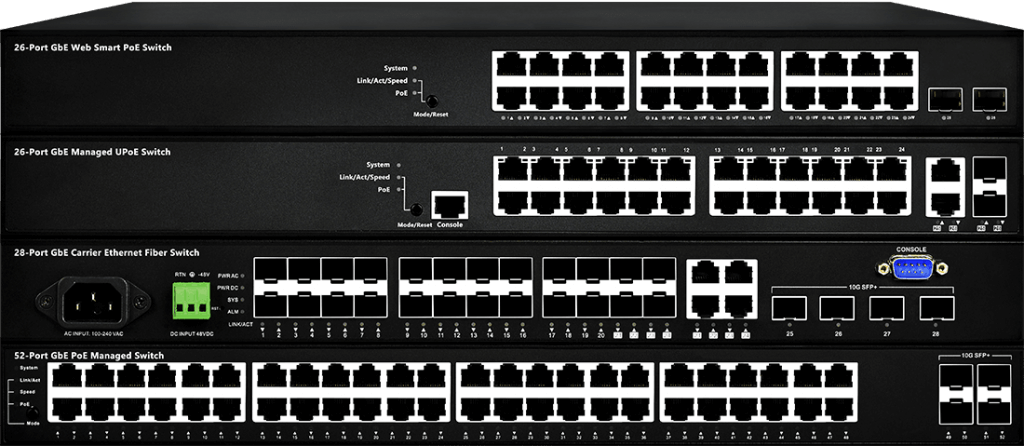
OEM / ODM Switch Customization Options
Hardware
Software
Customization that best meets your business needs Switch UI
SW Customization Service to integrate Third-Party management software.
When we embed Device Management System to the switch, a new era of possibilities begins. One where IT administrators are empowered with system of easy-to-use, and where maintenance is effortless and troubleshooting works in a moment.
One UI & iPush enable your business to operate switches in ways never before possible.
Easy Technical Support Online without client computer and third party remote control software.
What's New in Our OEM / ODM Products and Solutions
Wireless PoE Solution
Reliable Partner for the Intelligent Solutions RubyTech provide various OEM/ODM PoE Switch for Wireless connectivity solution, and makes the difference by utilizing its decades of networking experience, a tier-1 verified PoE/PoE+/PoE++, and by providing exceptional EMI/EMS levels protection, such as 6KV surge and outdoor IP67 PoE Switches. With these core strengths of flexibility and competitively, RubyTech has enabled its ODM customers to win key projects in a diverse range of industries. With its focus on delivering these ODM customization values, RubyTech’s [...]
ODM Customization Service for PoE NVR
ODM Customization Service for PoE NVR with built-in PoE++ ODM Customization Service for PoE NVR with built-in PoE for Security Providers to deliver suitable surveillance solution to any small or medium-sized business Design, Manufacturing, and Service Partner in Taiwan. Industry’s first All-in-One NVR integrated with managed switch and changeable M-ATX motherboard for next-gen NVR application. Advanced Switch API/GUI and VMS/CMS Integration, in order to create a next-gen compregensive management system, enhanced device-layer health check and diagnostic capability. Enhanced Trouble Shooting / Maintenance, value-added to [...]
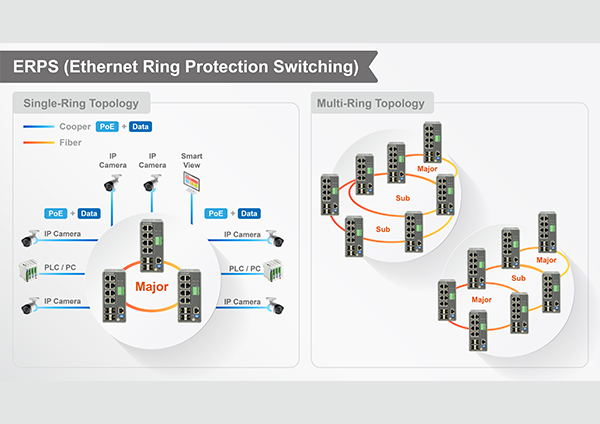
Ethernet Ring Protection Switching Solution
Ethernet Ring Protection Switching, or ERPS, is an effort at ITU-T under G.8032 Recommendation to provide sub-50ms protection and recovery switching for Ethernet traffic in a ring topology and at the same time ensuring that there are no loops formed at the Ethernet layer. G.8032v1 supported a single ring topology and G.8032v2 supports multiple rings/ladder topology. ERPS specifies protection switching mechanisms and a protocol for Ethernet layer network (ETH) rings. Ethernet Rings can provide wide-area multipoint connectivity more economically due [...]
IGS-2700 and IPGS-2700 series industrial switches
IGS-2700 and IPGS-2700 Series Industrial L2+ Managed GbE Switches [...]